Terraform Cloud
Leveraging Terraform Cloud and Sentinel for Bridgecrew scans
Bridgecrew has a native integration with Terraform Cloud that leverages Sentinel for policy controls. This means any commit that is pushed to Terraform Cloud will run through a Bridgecrew scan, identifying policy violations, blocking misconfigured builds, and detecting drift, all from the same place that you collaborate on Terraform templates, automate deployments, and store state.
Sentinel is a paid add-on. If you want to try this out for free, HashiCorp does offer a free trial. If you prefer not to sign up for the trial, feel free to skip this section and the “drift detection” section.
To sign up for the free trial of Terraform Cloud’s Team & Governance plan, go to your Terraform Cloud instance. In the top navigation, select “Settings” and “Plan & Billing.” Choose the “Trial Plan” option. You should see Policies and Policy Sets show up in the left navigation menu.
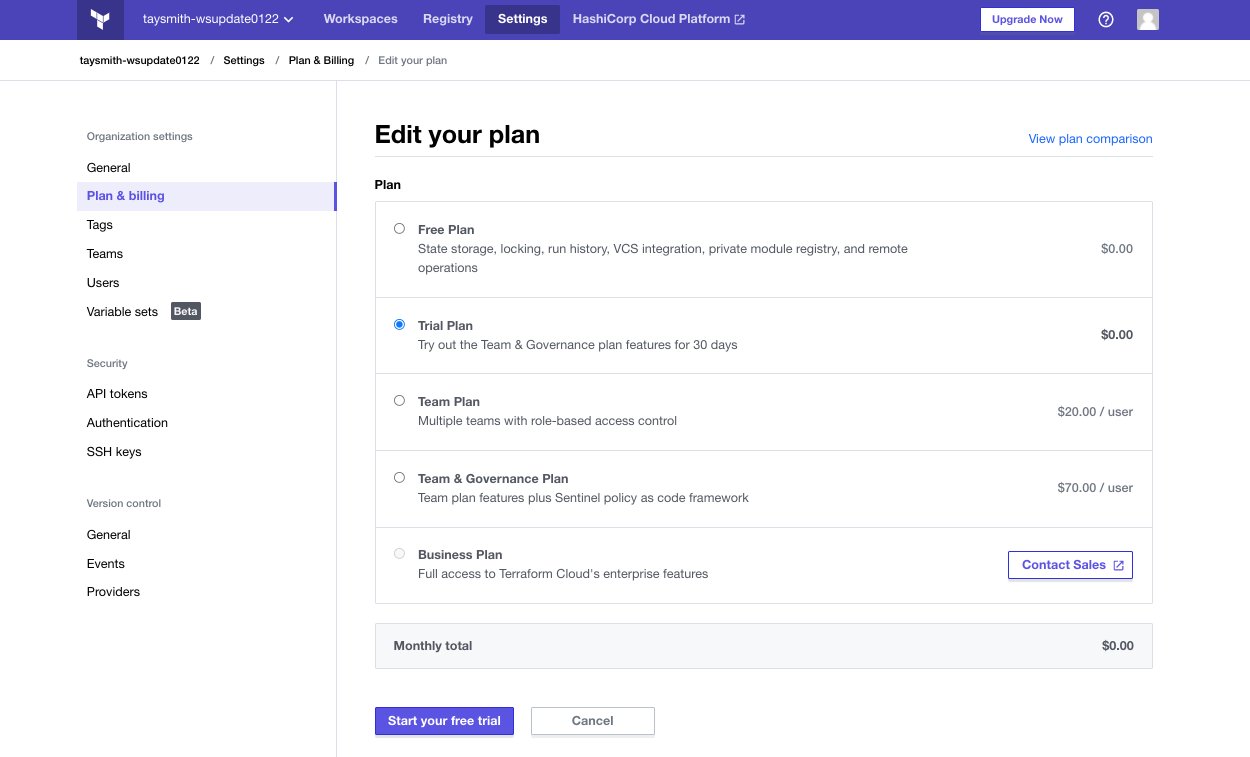
You need to add your TerraGoat repository to Terraform Cloud. Go to “Workspaces” and select “Create one now.”
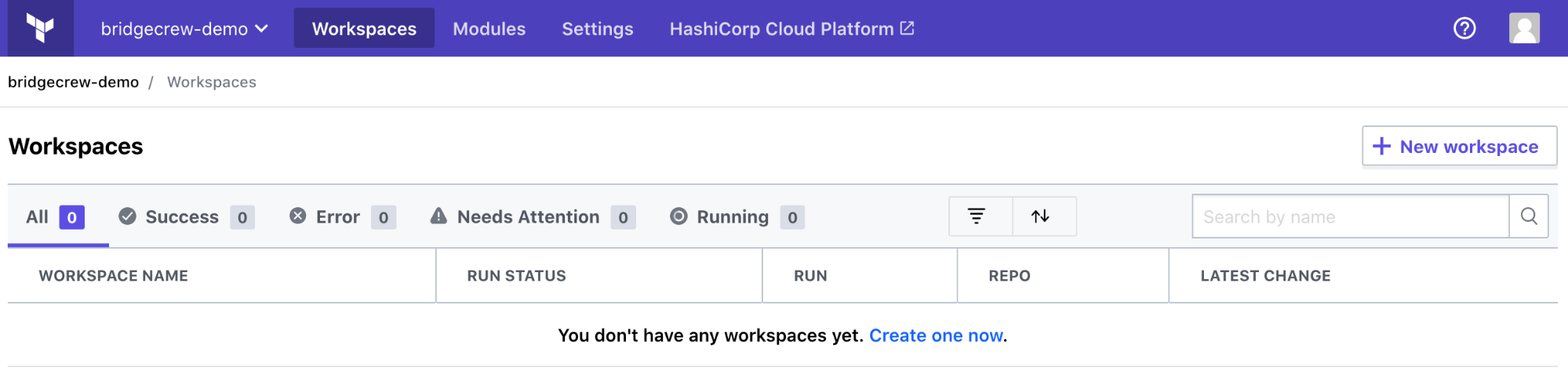
Select “Version control workflow”:
Select “GitHub," then “github.com,” and choose your TerraGoat repository we previously forked:
Name the workspace terragoat and open the “Advanced options” and add the directory /terraform/simple_instance/ (we’ll be adding that directory later). This will focus the scans to just the Azure templates. Turn on “Automatic speculative plans” and select “Create workspace”:
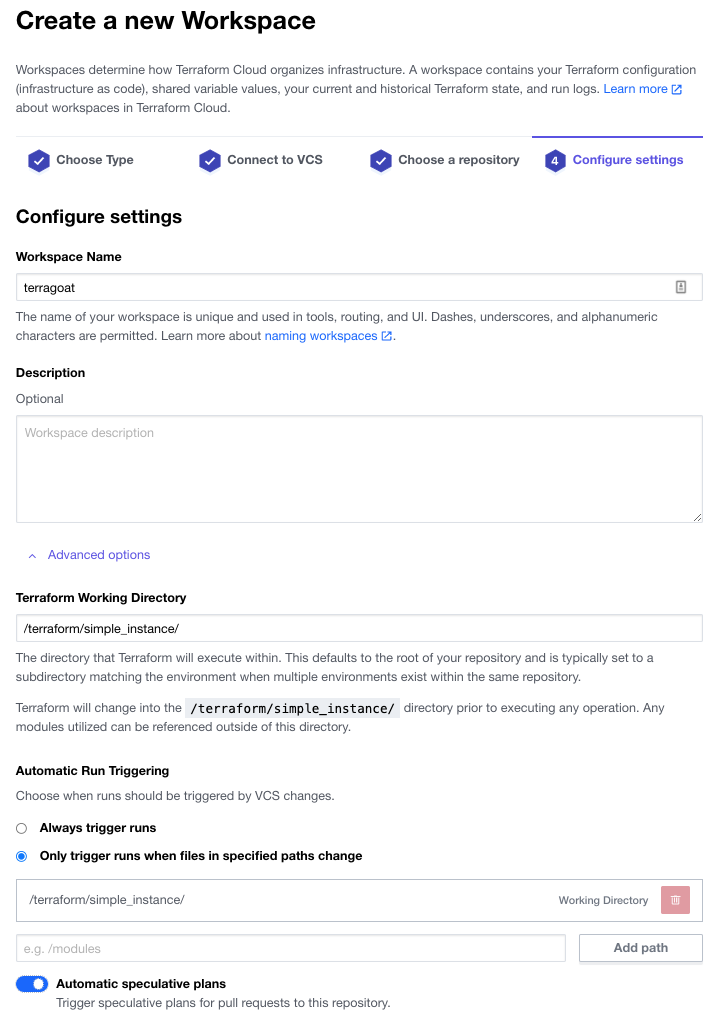
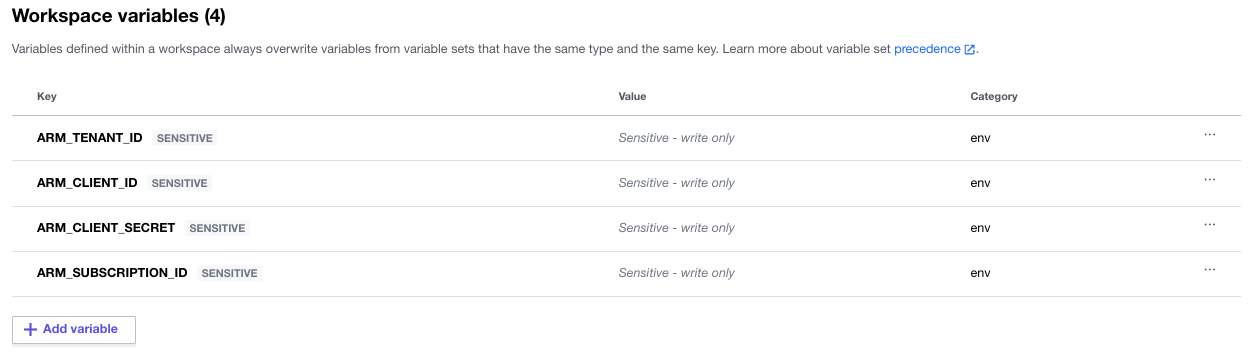
Select “Configure variables” and add your ARM API variables as follows:
- ARM_TENANT_ID - The
tenantfield when you created your Contributor Service Account - ARM_CLIENT_ID - The
appIdfield when you created your Contributor Service Account - ARM_CLIENT_SECRET - The
passwordfield when you created your Contributor Service Account - ARM_SUBSCRIPTION_ID - The
idfield from the Account List
If you aren’t sure where to find the keys, go back to the Azure setup step or refer to this guide.
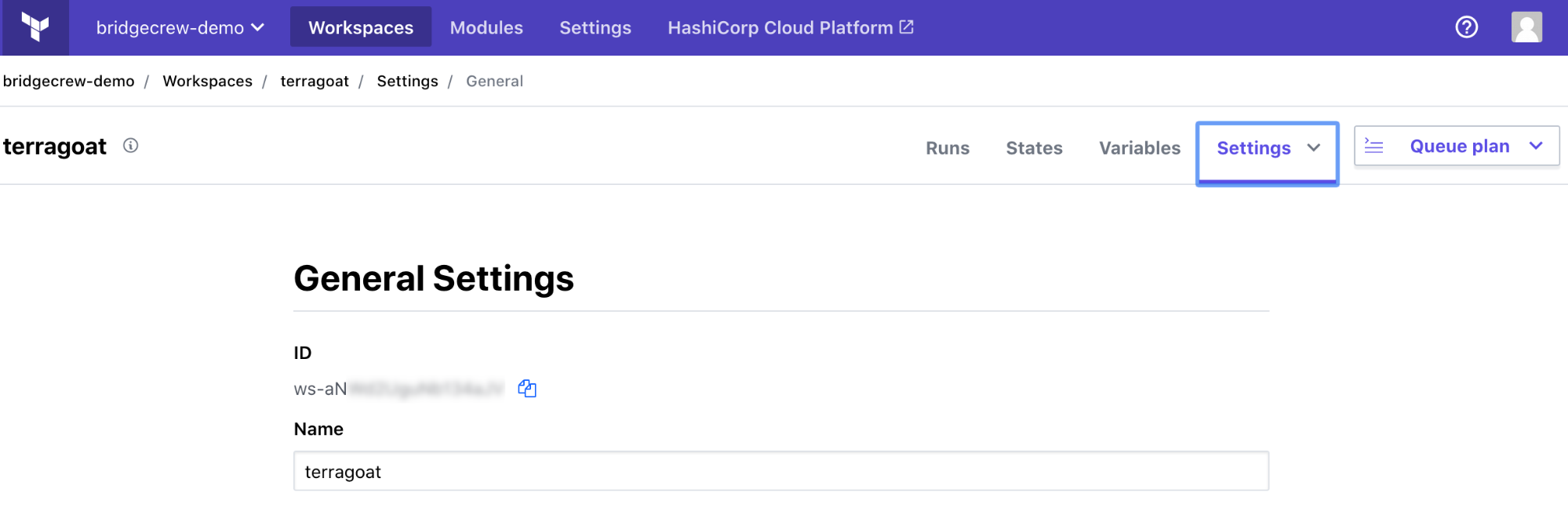
Go to the Workspace Settings and select General. From this settings screen, grab your workspace ID for the next step.
Grab the API token from Terraform Cloud for the integration. Go to the API token menu (User -> Settings -> Tokens) and select “Create an API token.”
Copy that API token for the next step.
Next, you’ll add the Bridgecrew integration. Head over to the Integrations screen in the Bridgecrew platform. Scroll down and select Terraform Cloud (Sentinel). Enter the token name tfc and choose “Create.” You don’t need to copy that key for this workshop. Paste your “Workspace ID,” “terragoat,” “TerraGoat,” and the API key from Terraform Cloud. Then click “Next.”
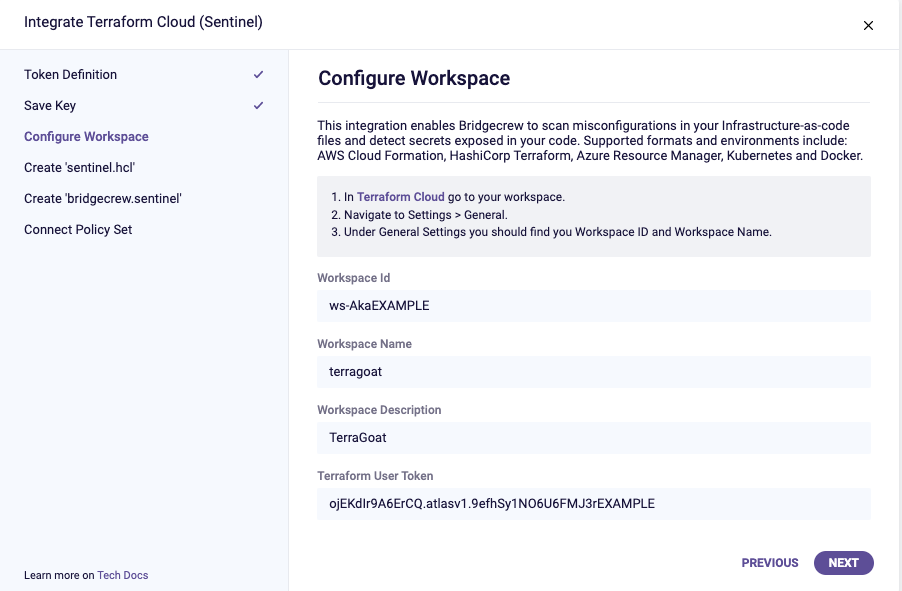
Normally, you would add a new repo with the Sentinel policies, but for the purpose of this workshop, we’re going to simplify this flow. You can click “Next” on the “Create ‘sentinel.hcl’” step.
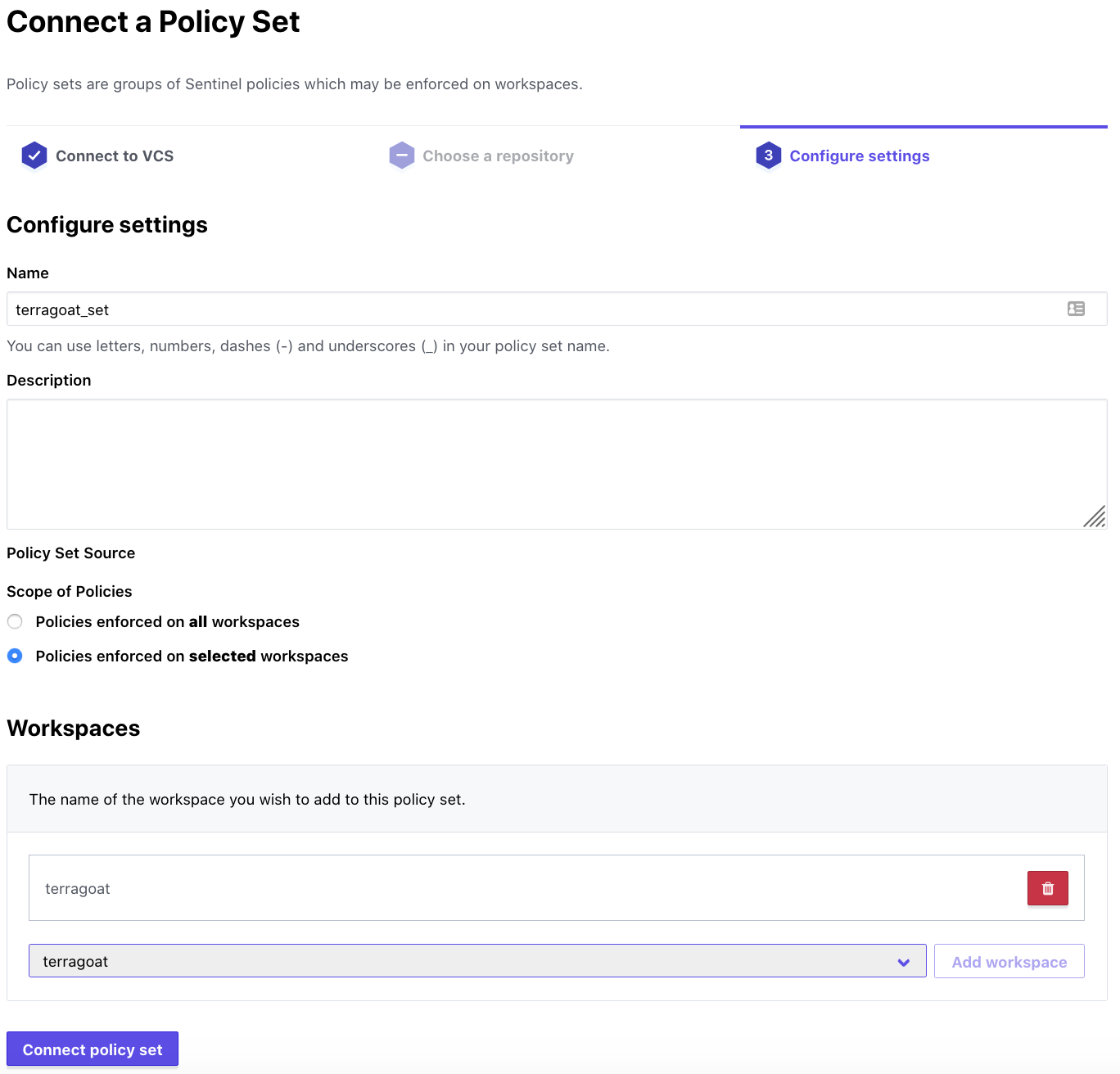
Copy the ‘bridgecrew.sentinel’ code and click “Next” in the wizard, then “Done.” Head back to Terraform Cloud. Go to Settings in the top nav and select “Policy Sets” and “Connect a new policy set”. You can create a versioned policy set, but for the sake of this workshop, go with “No VCS connection.”. Name your setting terragoat_set and choose the terragoat workspace and select “Connect policy set”.
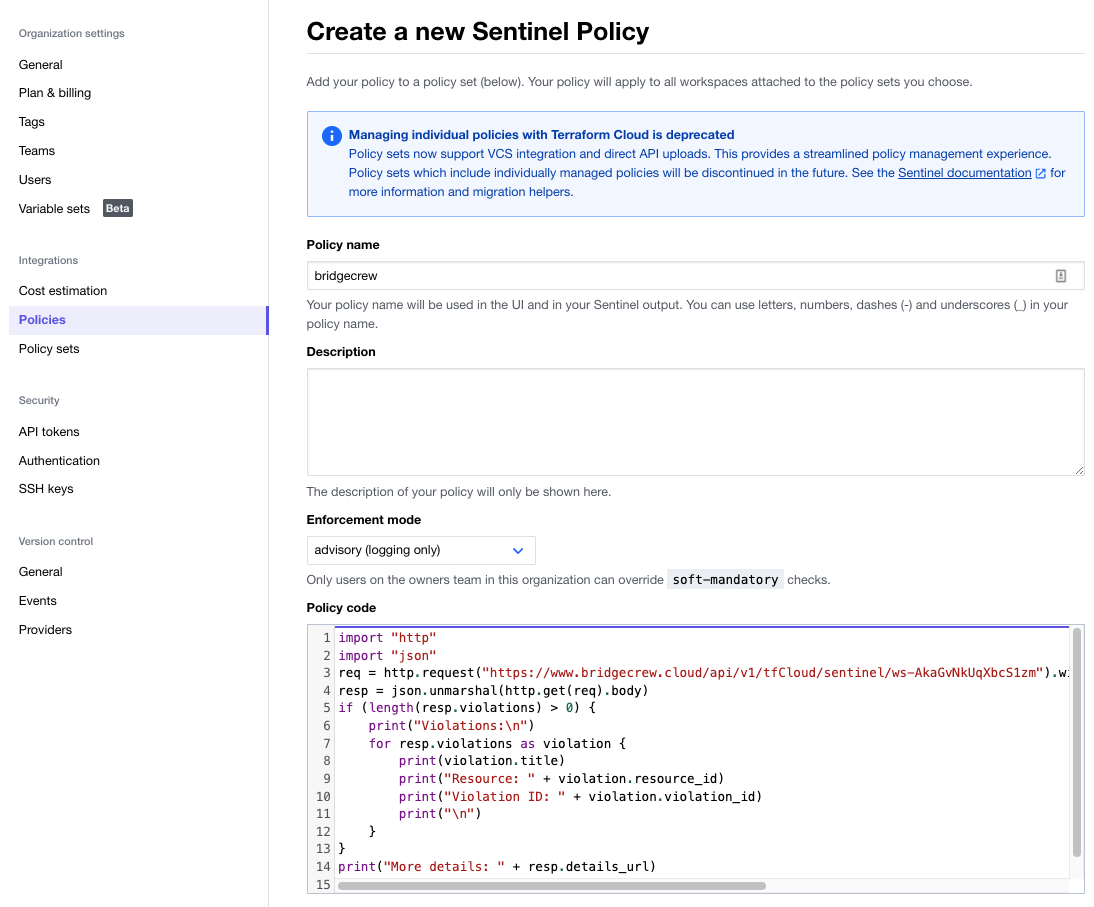
Then, select “Policies.” Click on “Create a new policy.” Name the policy bridgecrew. The “Enforcement mode” will determine whether builds are blocked (hard-mandatory) by violations of Sentinel policies, in this case sourced from Bridgecrew, are blocked but with an override (soft-mandatory), or just provide the violations but don’t block. For the purpose of this workshop, we know there are violations but we want to deploy them anyway. Set the mode to advisory (logging only).
Paste the code you copied in the Bridgecrew integration page and paste it into the “Policy code” section. Under “Policy Sets,” choose terragoat_set from the drop down, then “Add policy set” and select “Create policy”:
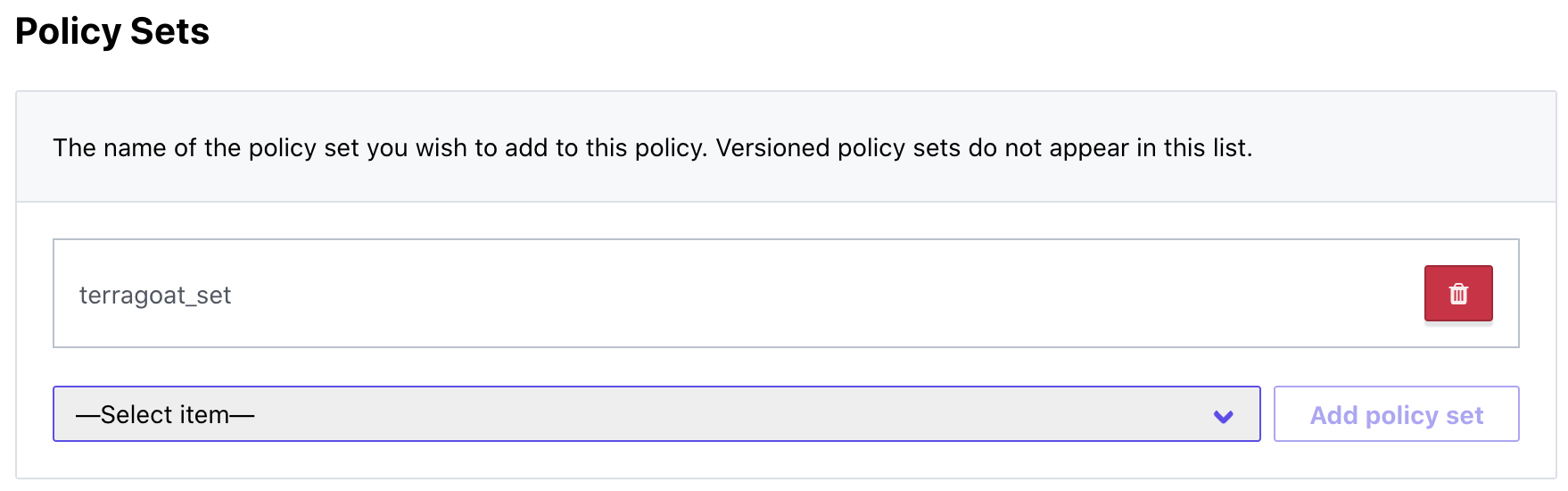
Finally, go to your workspace’s main page and under “Actions” select “Start new plan”; don’t worry if it fails, this just primes the runs to be automated with future GitHub pull requests.
Your Terraform Cloud integration is ready to go!