Run Checkov CLI locally
To demonstrate what kinds of security and compliance errors Bridgecrew can identify in CloudFormation templates, we’ll start by using Checkov CLI and send the results to the Bridgecrew platform.
Make sure you are in the cfngoat directory from the previous step, copy your unique Bridgecrew API token, and scan the cfngoat.yaml file:
checkov -f cfngoat.yaml --bc-api-key $YOUR_BC_API_KEY --repo-id bridgecrewio/cfngoat --branch main
You can also scan entire directories with -d <path>:
checkov -d . --framework cloudformation --bc-api-key $YOUR_BC_API_KEY --repo-id bridgecrewio/cfngoat --branch main
The results will show all the failed checks and link to a guide explaining the cause and how to fix them. Note the output also includes the filename and snippet of code that is misconfigured:
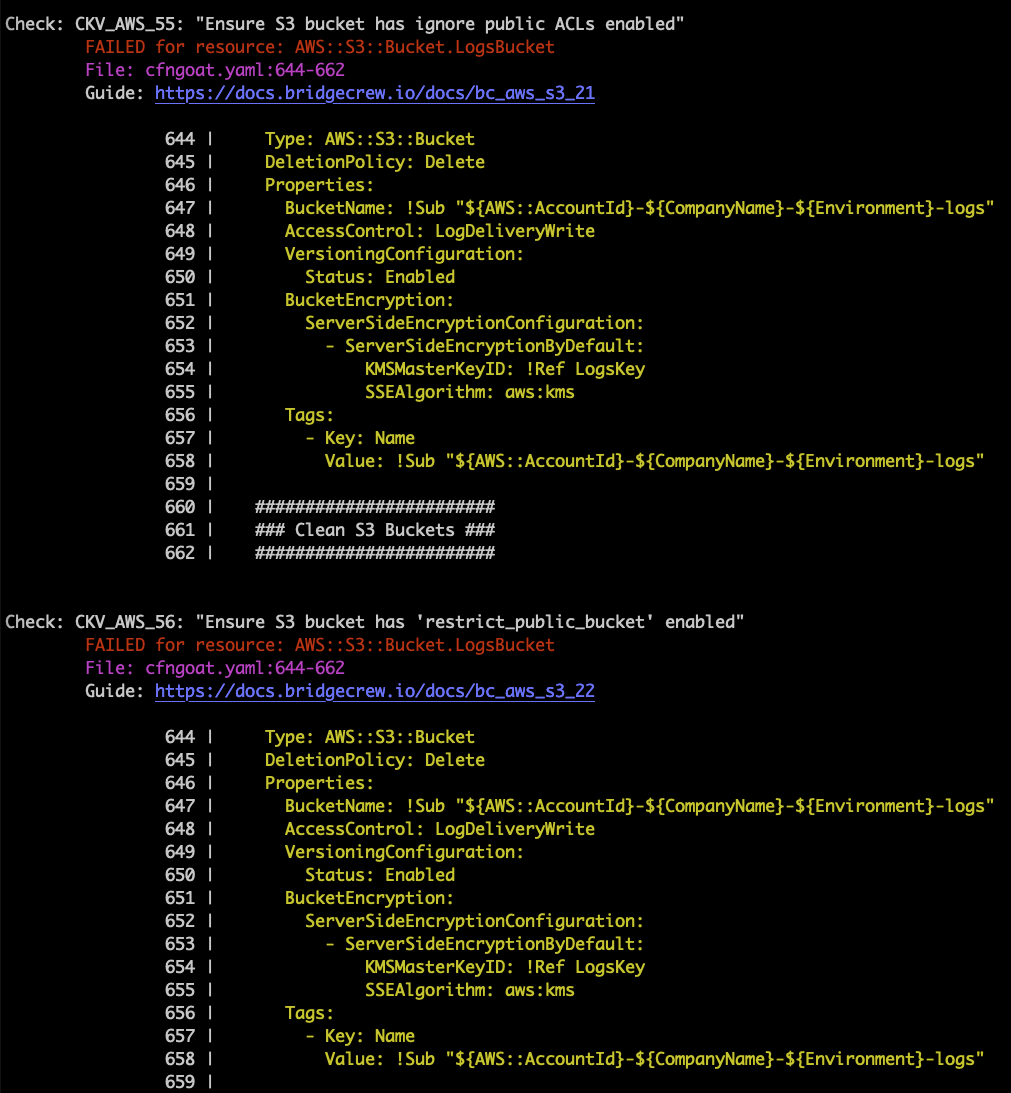
As you can see in the highlighted CLI output above, our demo CloudFormation repository has failing checks for two policies:
- Ensure S3 bucket has ignore public ACLs enabled
- Ensure S3 bucket ‘RestrictPublicBucket’ is set to True
To get the list of policies builtin to your version of checkov, use -l or –list:
checkov --list
Bridgecrew policies
In many instances, when testing locally with the Checkov CLI, you may only be interested in running just a few checks. In that case, you can add the -c or --check option:
checkov -f cfngoat.yaml -c CKV_AWS_55,CKV_AWS_56
Alternatively, if you want to run all but a few checks, use the --skip-check option:
checkov -f cfngoat.yaml --skip-check CKV_AWS_55,CKV_AWS_56
Next, let’s inspect these results in the Bridgecrew dashboard.