Reviewing our pipeline results
Your new CodePipeline will immediatley start running your CodeBuild job against the latest commit in your GFNGoat Repository.
You will be taken to the Pipeline Jobs page where you will see the progress as CodeBuild checks out the latest commit from GitHub and starts our job to run Bridgecrew against the CloudFormation configuration.
Below we see the Pipeline sucessfully created and starting to run:
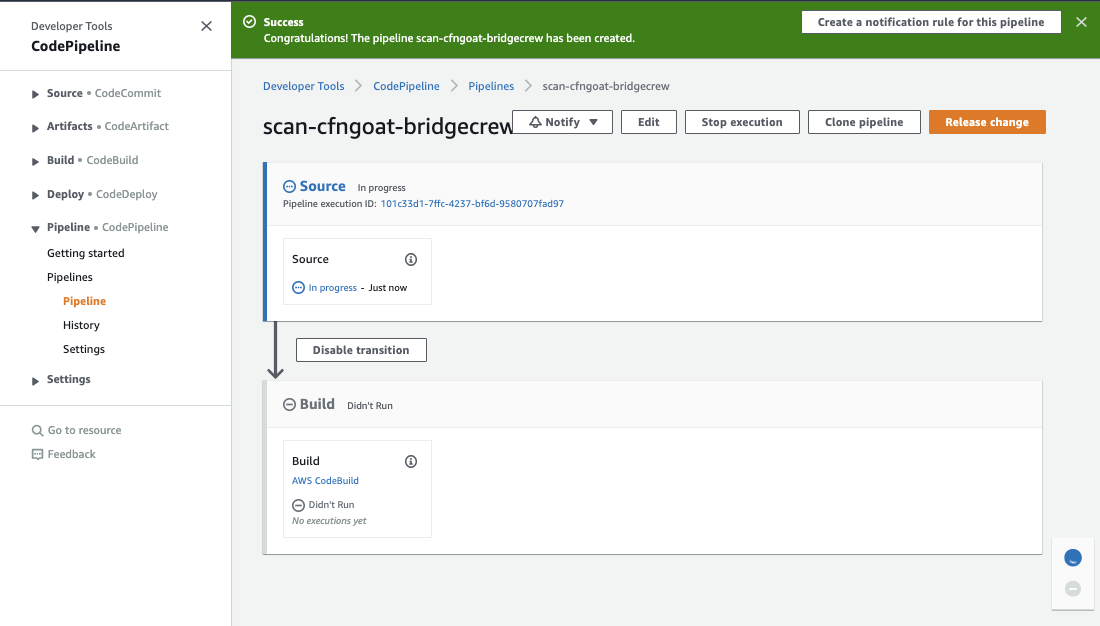
If everything goes as intended, the pipeline should fail at the build stage since the CfnGoat code is purposely designed with security flaws. Only when the issues are fixed will the pipeline status turn to green.
By blocking the committed code from making it to any “Deploy” steps, we can prevent vulnerable infrastructure from making its way to any AWS account, be it test or prod and helping to satisfy the requirements of the AWS Shared Responsibility Model
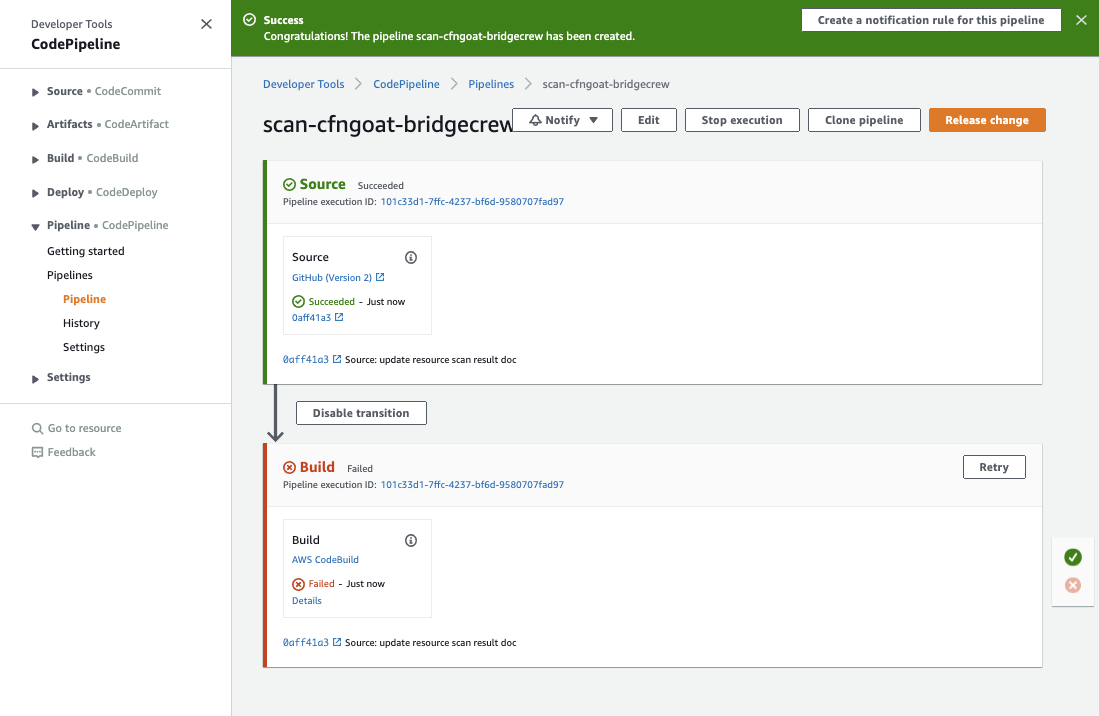
Dig into the failed build Details and select the link to execution details:
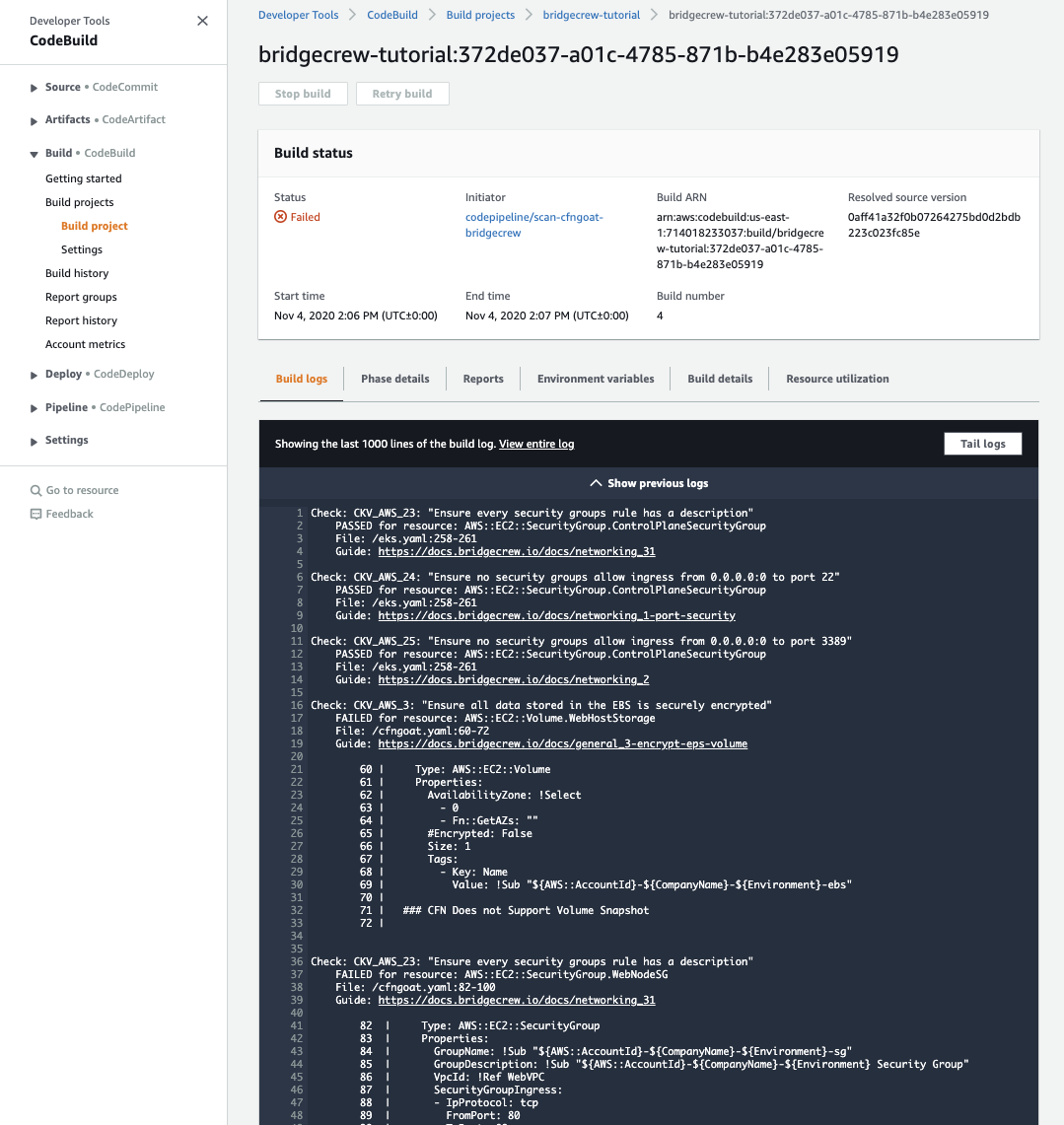
Here we are provided a link to our build logs, revealing the security violations and why Bridgecrew blocked the build:
Navigating to Codebuild > Report Group, we can also see a simple graph of failed and passed checks with an easier-to-read output of all failed checks.
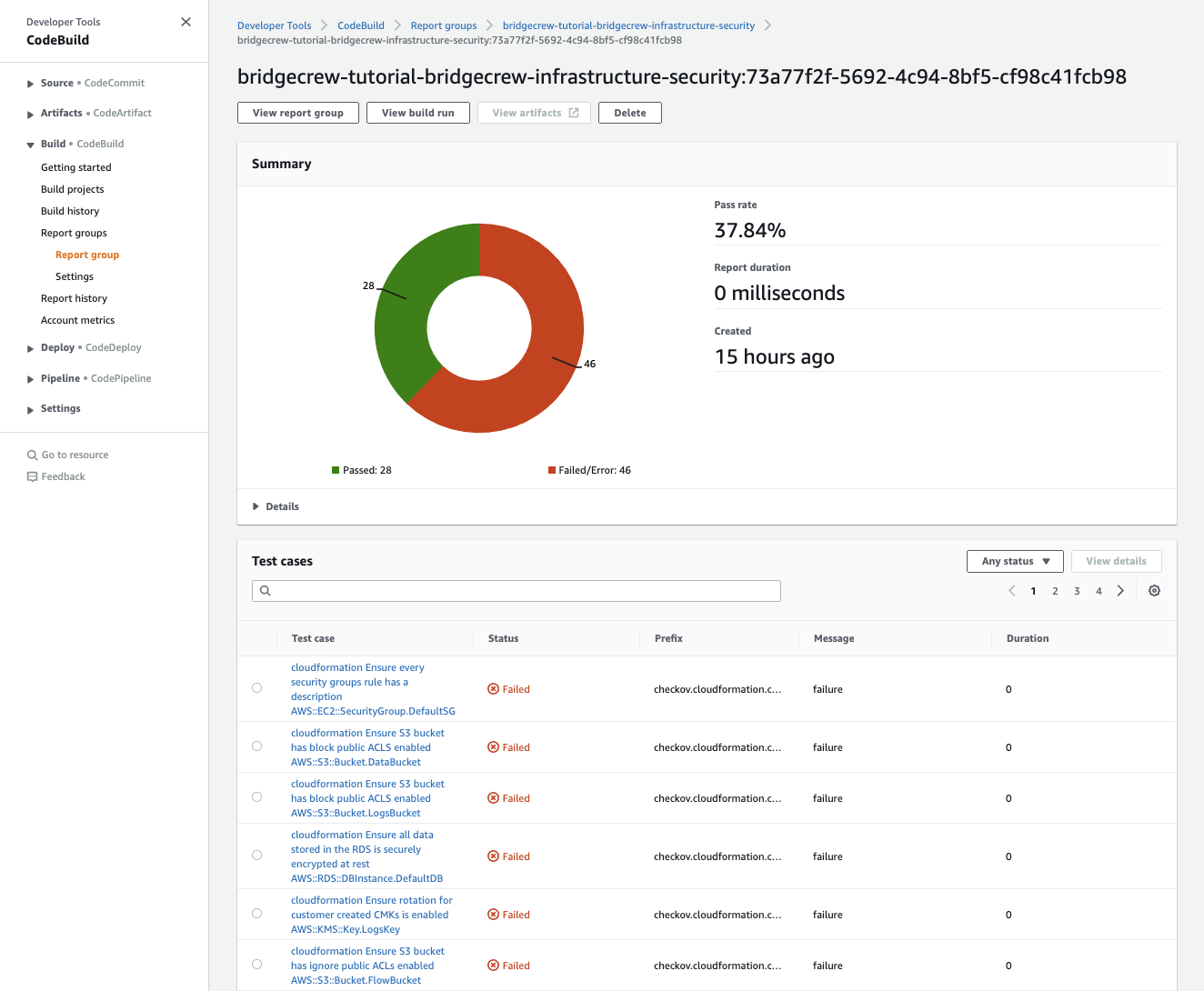 “AWS CodeBuild JUnit output”
“AWS CodeBuild JUnit output”
Congratulations!
You’ve just automated security scanning of your infrastructure as code into a developer-friendly CI/CD pipeline.
In the next module, we’ll look at how to investigate and fix these issues, as well as providing more tips for integrating security into the developer workflow without causing friction.